Contents
CentOS7 offers a completely different approach to resetting a forgotten root password than the it’s earlier distro of CentOS6.x. Here are multiple approaches that was tested on CentOS Linux release 7.2.1511 (Core) with success. The last one being one that I combined from the many different approaches into fewer steps.
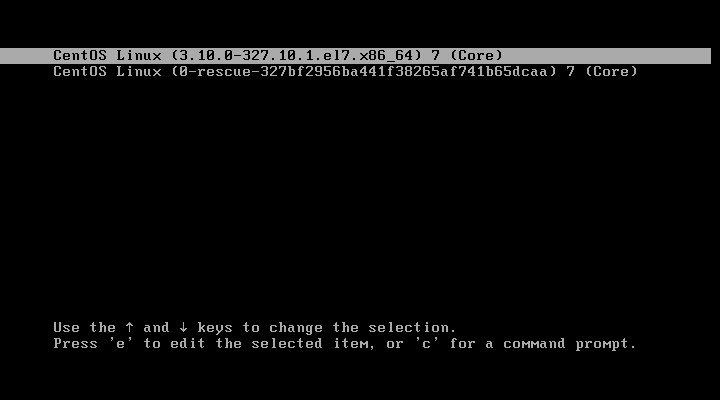
Reset the Root password (version 1
Reboot the system to the grub2 menu.
Press e to edit the selected item.
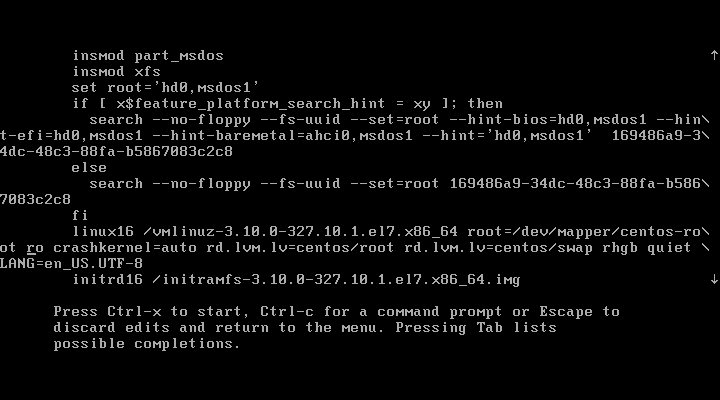
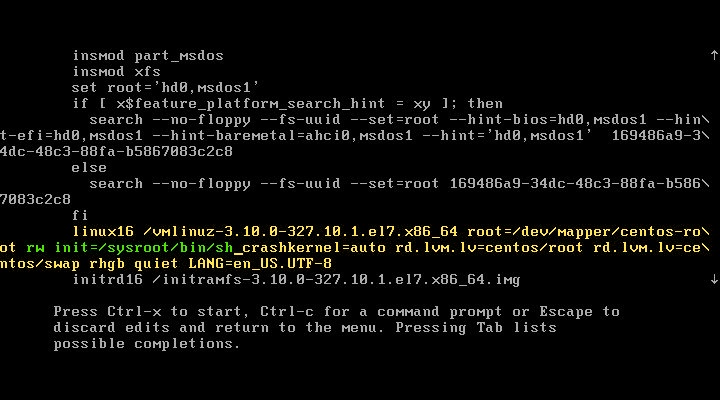
Scroll to the section linux16 and replace the ro with rw init=/sysroot/bin/sh.
Some systems (notably virtual machines) may have problems displaying correct output when you boot using this procedure. Some characters or even entire lines may be hidden, making the shell difficult to use. To solve this problem, delete the rhgb command from the linux line.
Press Ctrl-x to start. the single user mode and access the command prompt.
To access the system.
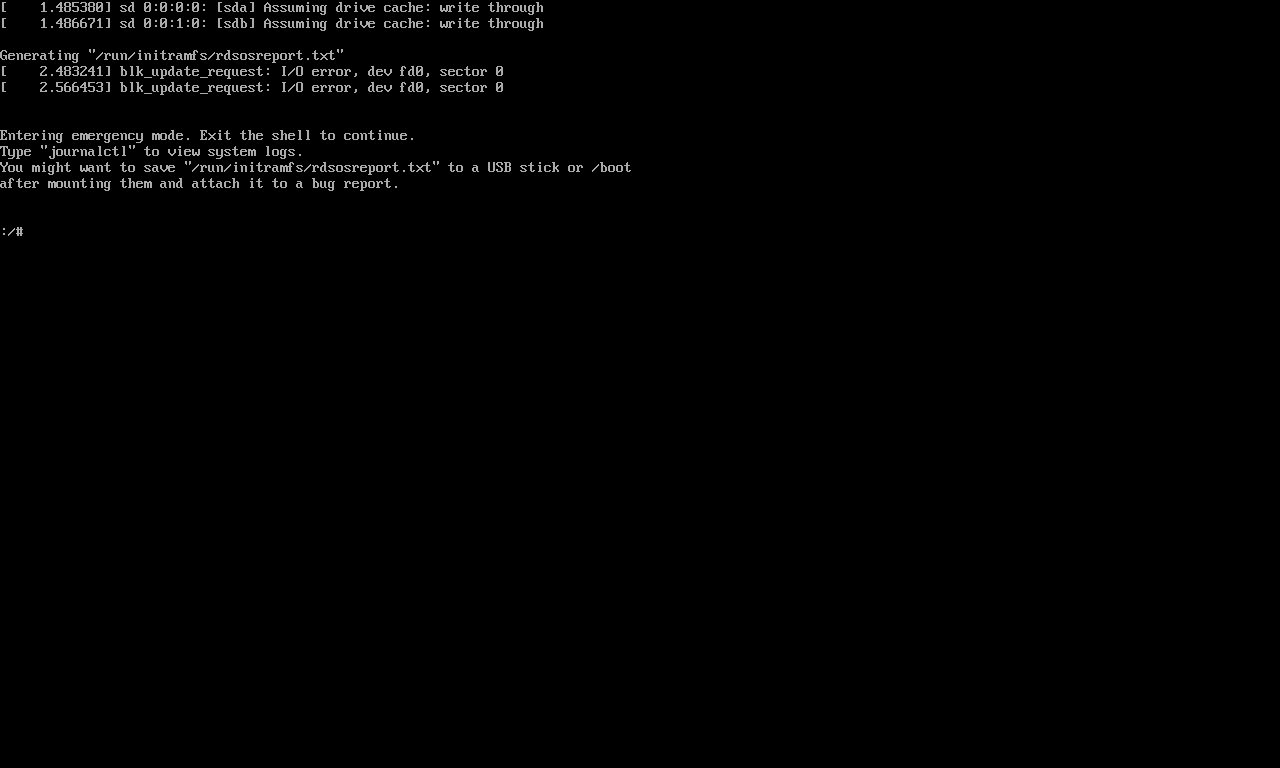
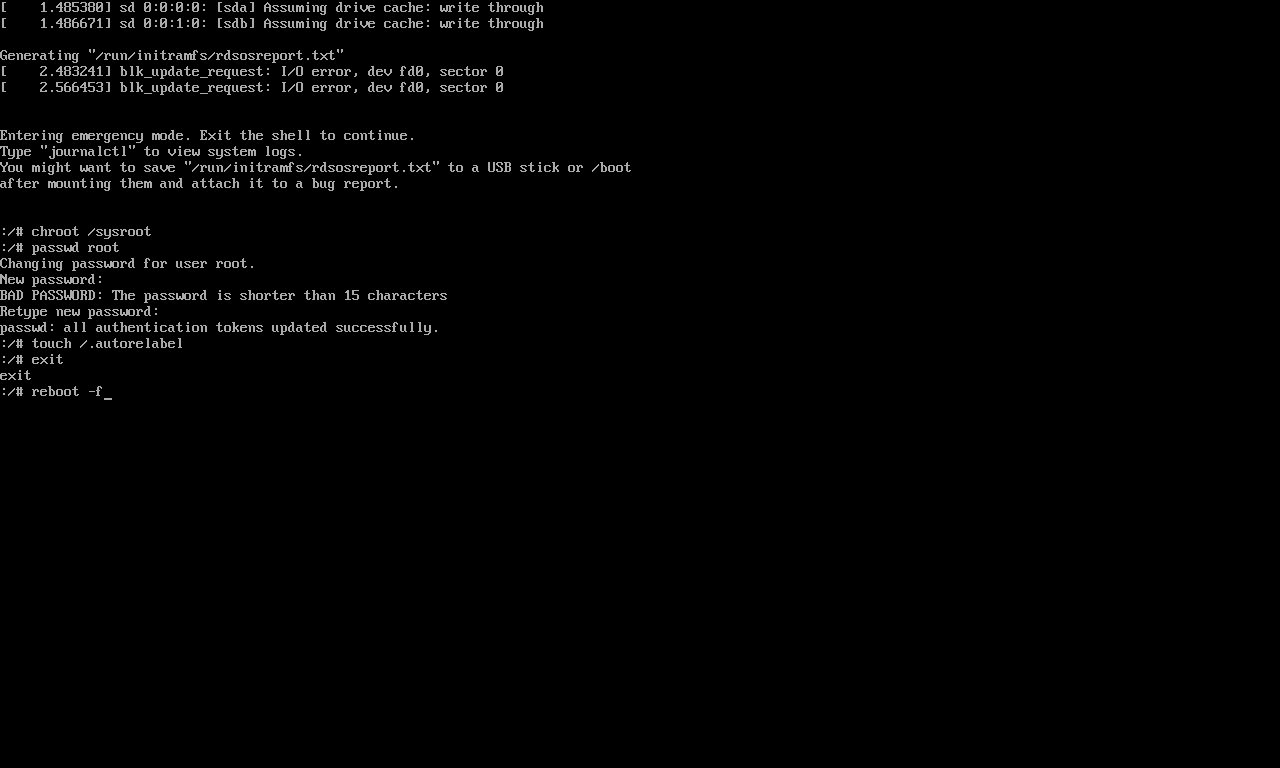
chroot /sysrootReset the root password.
passwd rootUpdate selinux
touch ./autorelabelExit the chroot environment
exitReboot the system
reboot -fReset the Root password (version 2
According to one comment, the official RHCSA 7 training describes the following procedure to work. This approach was tested on CentOS Linux release 7.2.1511 (Core) with success.
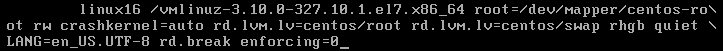
Append “rd.break” to the kernel command line that starts with linux16 (this will break just before control is handed from the initramfs to the actual system) (sometimes it is needed to delete also everything after “…mapper/rhel-root ro” and append here)
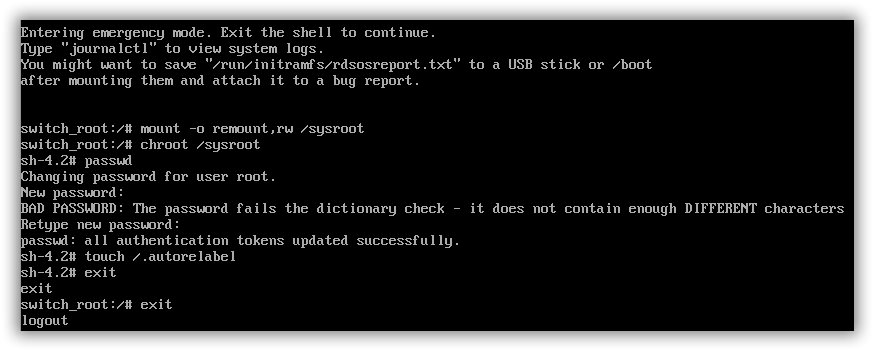
mount -o remount,rw /sysroot
chroot /sysroot
passwd
touch /.autorelabel
exit
exitReset the Root password (version 3)
This one if from the Red Hat documentation. Tested on 8/21/2016.
- Boot your system and wait until the GRUB2 menu appears.
- In the boot loader menu, highlight any entry and press e to edit it.
- Find the line beginning with
Linux. At the end of this line, append the following:
init=/bin/sh- Press F10 or Ctrl+X to boot the system using the options you just edited. Once the system boots, you will be presented with a shell prompt without having to enter any user name or password:
sh-4.2#- Load the installed SELinux policy:
sh-4.2# /usr/sbin/load_policy -i- Execute the following command to remount your root partition:
sh-4.2# mount -o remount, rw /- Reset the root password:
sh-4.2# passwd root- Remount the root partition as read-only.
sh-4.2# mount -o remount, ro /- Reboot the system.
exitReset the Root password (version 4)
Alright, this one is my test. Worked for me, but doesn’t mean it will for you. It was a matter of curiosity as there seems that many variables may be altered to achieve the end goal of changing the forgotten root password.
- Boot your system and wait until the GRUB2 menu appears.
- In the boot loader menu, highlight any entry and press e to edit it.
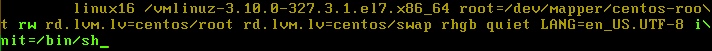
- Find the line beginning with
linux. Replace therowithrw. and at the end of this line, append the following:
init=/bin/sh- Press F10 or Ctrl+X to boot the system using the options you just edited. Once the system boots, you will be presented with a shell prompt without having to enter any user name or password:
sh-4.2#- Load the installed SELinux policy:
Since this is an early boot stage for SELinux, the context type on /etc/shadow will be incorrect. If you reboot without loading the SELinux or modifying the context no one will be able to log in. Ensure that the context type is set correctly.
sh-4.2# /usr/sbin/load_policy -i- Reset the root password:
sh-4.2# passwd root- Reboot the system.
exitReset the Root password (version 5
Alright, this one is my test. Worked for me, but doesn’t mean it will for you. It was a matter of curiosity as there seems that many variables may be altered to achieve the end goal of changing the forgotten root password. This one relies heavily on one variation found on CertDepot with an additional change in GRUB2 that removes the need to use the mount / remount commands.
- Boot your system and wait until the GRUB2 menu appears.
- In the boot loader menu, highlight any entry and press e to edit it.
- Find the line beginning with
linux16. Replace therowithrw. and at the end of this line, append the following:
rd.break enforcing=0- Press F10 or Ctrl+X to boot the system using the options you just edited. Once the system boots, you will be presented with a shell prompt without having to enter any user name or password:
switch_root:/#- Change root.
switch_root:/# chroot /sysroot- Reset the root password:
sh-4.2# passwd root- Logout.
sh-4.2# exit
switch_root:/# exitThe system should now be on a login screen. Once logged in. Type the following two commands to complete the password change process.
restorecon /etc/shadow
setenforce 1However, to see the changes along the way use ls -Z to review the labels and use getenforce to check the status of SeLinux.
[root@c7linux ~]# ls -Z /etc/shadow
----------. root root system_u:object_r:unlabeled_t:s0 /etc/shadow
[root@c7linux ~]# restorecon /etc/shadow
[root@c7linux ~]# ls -Z /etc/shadow
----------. root root system_u:object_r:shadow_t:s0 /etc/shadow
[root@c7linux ~]# getenforce
Permissive
[root@c7linux ~]# setenforce 1
[root@c7linux ~]# getenforce
EnforcingAppendix
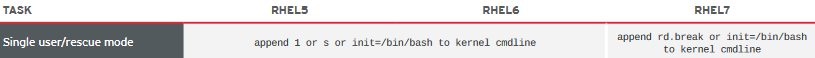
From the Red Hat Enterprise Linux 5,6, and 7 Common Administrative commands “cheat sheet” under Kernel, Boot, and hardware, the Single user/rescue mode task for RHEL7 may append rd.break or init=/bin/bash to the kernel cmdline.
Since /bin/sh is a symbolic link to /bin/bash, it too may be used.
[root@c7linux opt]# ls -Atlr /bin/ | grep -w "bash"
-rwxr-xr-x. 1 root root 960376 Nov 20 2015 bash
lrwxrwxrwx. 1 root root 4 Mar 17 08:07 sh > bash
According to Red Hat RHCSA/RHCE 7 Cert Guide: Red Hat Enterprise Linux 7 (EX200 and EX300)
- rd.break This stops the boot procedure while still in the initramfs stage. This option is useful if you do not have the root password available.
- init=/bin/sh or init=/bin/bash This specifies that a shell should be started immediately after loading the kernel and initrd. This is a useful option, but not the best option, because in some cases you’ll lose console access or miss other functionality.
While booting a /run/initramfs/rdsosreport.txt report is generated. While leaving the GRUB2 menu in its default configuration, the following can be read from the report.
59 1 253:0 / /sysroot ro,relatime shared:22 - xfs /dev/mapper/centos-root rw,attr2,inode64,noquota
/dev/mapper/centos-root /sysroot xfs ro,relatime,attr2,inode64,noquota 0 0With a small change to the line that begins with linux16. Replace the ro with rw. Note that this is now read write.
/59 1 253:0 / /sysroot rw,relatime shared:22 - xfs /dev/mapper/centos-root rw,attr2,inode64,noquota
dev/mapper/centos-root /sysroot xfs rw,relatime,attr2,inode64,noquota 0 0Source(s)
- https://www.unixmen.com/reset-root-password-centos-7/
- http://www.tecmint.com/reset-forgotten-root-password-in-centos-7-rhel-7/
- https://access.redhat.com/documentation/en-US/Red_Hat_Enterprise_Linux/7/html
- Installation_Guide/chap-basic-system-recovery.html#sect-rescue-mode-reset-root-password
- https://www.certdepot.net/rhel7-interrupt-boot-gain-access-system/
- https://access.redhat.com/sites/default/files/attachments
- rhel_5_6_7_cheatsheet_27x36_1014_jcs_web.pdf
- Vugt, Sander Van. Red Hat RHCSA/RHCE 7 Cert Guide: Red Hat Enterprise Linux 7 (EX200 and EX300). N.p.: n.p., n.d. Print.