Contents
Securing a CentOS 7 install doesn’t have to be tough. Code already exists, we just have to find it and execute it.
Prerequisites
yum install openscap scap-security-guide -y
Verification
The version of the scap-security-guide that was tested is 0.1.40.
Version 0.1.43 has removed the DISA STIG from the CentOS guide ssg-centos7-ds.xml; however, there is a work-a-round. Article coming soon.
scap-security-guide.noarch 0.1.40-13.el7.centos @updates
Test
The purpose of this test is to determine if the scap-security-guide supports DISA STIG.
oscap info /usr/share/xml/scap/ssg/content/ssg-centos7-ds.xml | grep -i disa
 Create an Ansible Script
Create an Ansible Script
Once it is confirmed that the version of scap-security-guide supports DISA STIG for CentOS, the Ansible script may be created.
oscap xccdf generate fix --fix-type ansible \ --profile xccdf_org.ssgproject.content_profile_stig-rhel7-disa \ --output stig-rhel7-role.yml \ /usr/share/xml/scap/ssg/content/ssg-rhel7-ds.xml
Execute Ansible Script
You may have to correct errors. I had to modify the script in at least five places to run the script.
ansible-playbook -i inventory.ini stig-playbook-result.yml
The results of the script.
PLAY RECAP ************************************************** 192.168.1.102 : ok=405 changed=48 unreachable=0 failed=1 skipped=49 rescued=0 ignored=5
Generate a Report
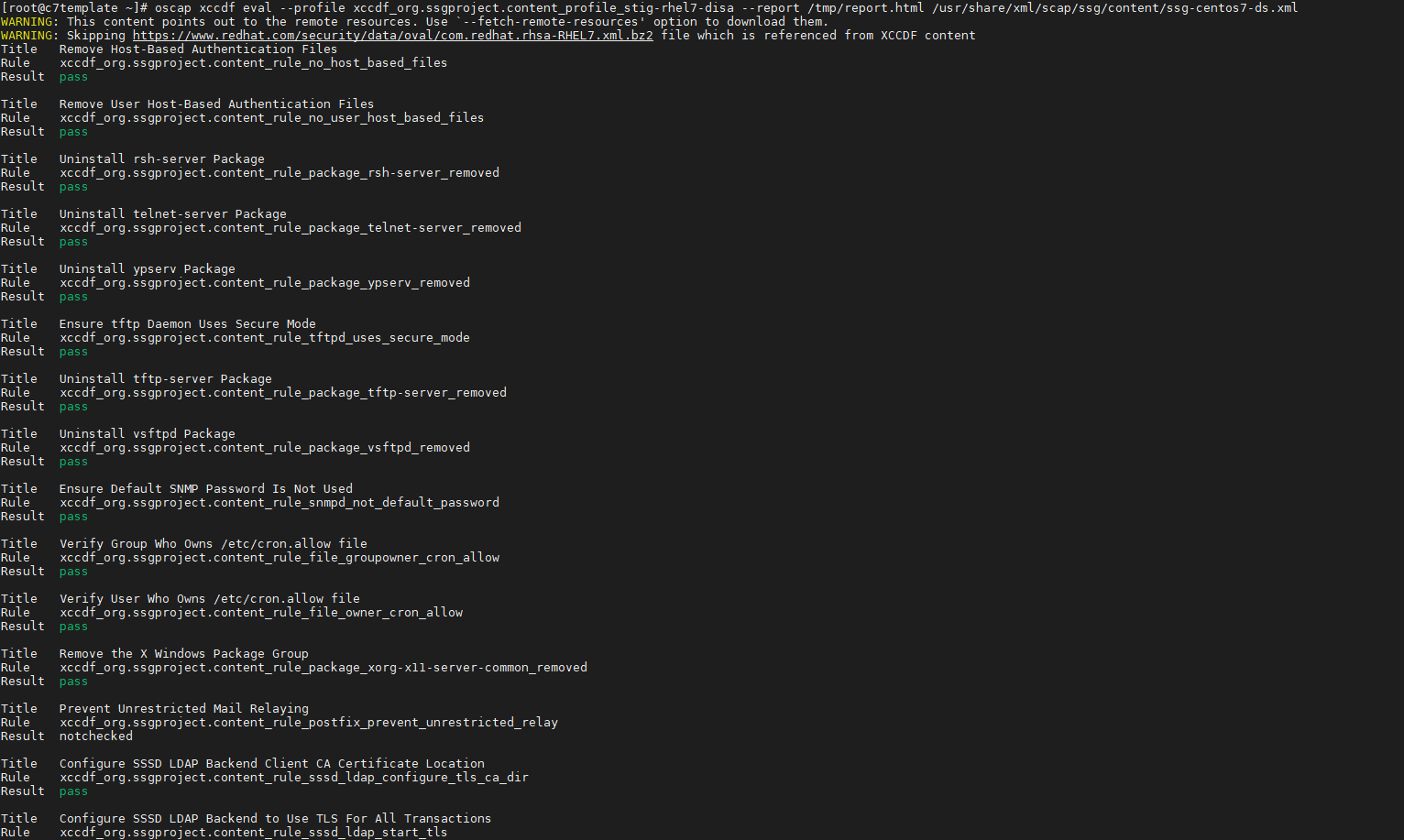
oscap xccdf eval --profile xccdf_org.ssgproject.content_profile_stig-rhel7-disa --report /tmp/report.html /usr/share/xml/scap/ssg/content/ssg-centos7-ds.xml
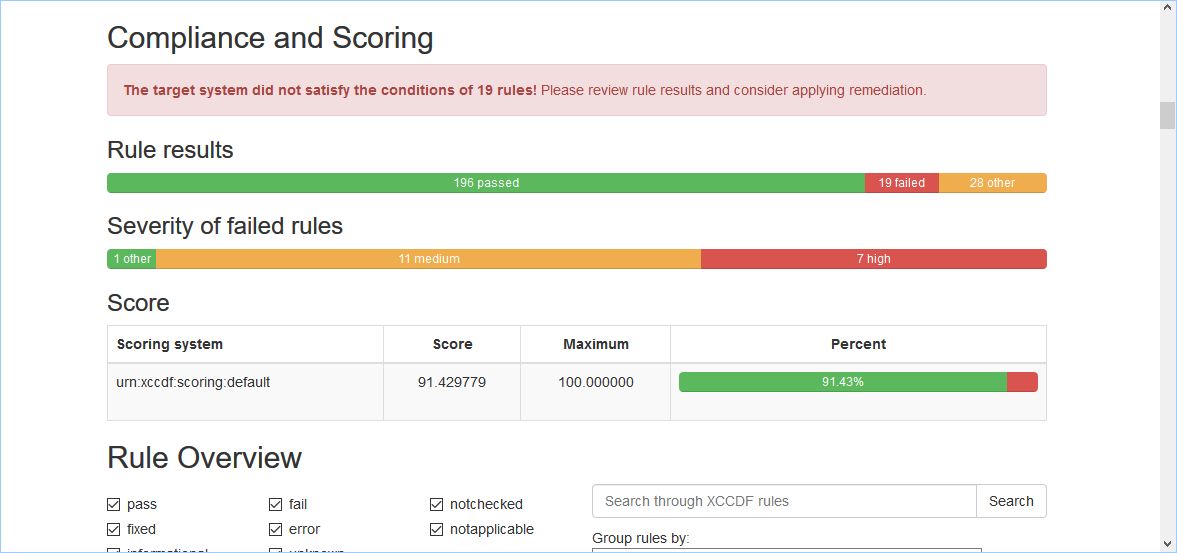
While the report is generating, the results will display on the screen as well as generate an html report.
The review the results.
Source(s)
- https://conklin.io/assessing-centos-7-with-openscap/
- https://www.redhat.com/en/blog/automating-security-compliance-ease
- https://galaxy.ansible.com/redhatofficial/rhel7_stig
- https://conklin.io/assessing-centos-7-with-openscap/