Contents
The scap-security-guide changes in format with each new guide. CentOS 8 is not fully represented within the guide. The XMLs provided differ in context, so the RHEL XML must be used to generate the report but requires a small patch to do so.
The CUI Profile
The ssg-rhel8-ds-1.2.xml contains the profile cui, while the one for ssg-centos8-ds-1.2.xml does not.
[root@admin scap-security-guide-0.1.53]# oscap info ssg-centos8-ds-1.2.xml | grep cui
[root@admin scap-security-guide-0.1.53]# oscap info ssg-rhel8-ds-1.2.xml | grep cui
Id: xccdf_org.ssgproject.content_profile_cui
Test System
Before getting started, the test system is a minimal install CentOS 8 virtual machine with custom partitions. It is so much easier to remediate some of these findings in advance, such as creating custom partitions.
/dev/mapper/vg01-root / xfs defaults 0 0 UUID=bdc30244-6182-47c6-abcf-df18ebeab327 /boot ext4 defaults 1 2 /dev/mapper/vg01-home /home xfs defaults 0 0 /dev/mapper/vg01-tmp /tmp xfs defaults 0 0 /dev/mapper/vg01-var /var xfs defaults 0 0 /dev/mapper/vg01-var_log /var/log xfs defaults 0 0 /dev/mapper/vg01-var_log_audit /var/log/audit xfs defaults 0 0 /dev/mapper/vg01-swap swap swap defaults 0 0
A few packages needed to get started.
dnf -y install git ansible unzip wget scap-security-guide openscap audit aide
SCAP Security Guide
There a couple of maintained versions of this guide. One by Red Hat and ComplianceAsCode on Github.
Download SCAP Security Guide
cd /opt wget https://github.com/ComplianceAsCode/content/releases/download/v0.1.53/scap-security-guide-0.1.53.zip unzip scap-security-guide-0.1.53.zip cd scap-security-guide-0.1.53
A small edit to allow the report to generate without errors. Search for <xccdf-1.2:platform idref=”cpe:/o:redhat:enterprise_linux:8″/> and remove cpe:/o:redhat:enterprise_linux:8.
sed -i.bak "s/<xccdf-1.2:platform idref.*//g" ssg-rhel8-ds-1.2.xml
Generate a before report. After running the ansible playbook, this command can be used to generate an after report.
oscap xccdf eval --profile xccdf_org.ssgproject.content_profile_cui --report /tmp/report-centos8-cui.html ssg-rhel8-ds-1.2.xml
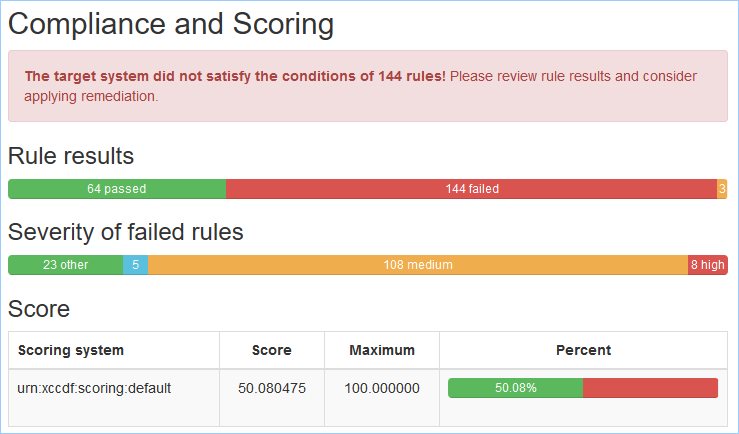
Pre-Remediation Results
The following snippit is from the generated report from above.
Alternately, without having to generate a report, the following command will provide a count which matches the value from the screenshot.
[root@admin scap-security-guide-0.1.53]# oscap xccdf eval --profile xccdf_org.ssgproject.content_profile_cui ssg-rhel8-ds-1.2.xml 2>&1 | grep -i ^Result | grep fail | wc -l 144
Ansible Playbook
The ansible playbook is located in the sub directory ansible. Once there, add ignore_errors to the playbook, otherwise the script will stop about half way through.
cd /opt/scap-security-guide-0.1.53/ansible sed -i.bak '/\- hosts: all/a \ \ ignore_errors: yes' rhel8-playbook-cui.yml
Run the playbook. Here are a few options.
# Test the script (using --check) ansible-playbook -i localhost, -c local rhel8-playbook-cui.yml --check # Test the script but remove options that you may not want to implement (using --check) ansible-playbook -i localhost, -c local rhel8-playbook-cui.yml --check --skip-tags \ accounts_passwords_pam_faillock_unlock_time,\ accounts_passwords_pam_faillock_interval,\ accounts_passwords_pam_faillock_deny,\ grub2_enable_fips_mode,\ configure_crypto_policy # Actual run with options removed. (remove the --check) ansible-playbook -i localhost, -c local rhel8-playbook-cui.yml --skip-tags \ accounts_passwords_pam_faillock_unlock_time,\ accounts_passwords_pam_faillock_interval,\ accounts_passwords_pam_faillock_deny,\ grub2_enable_fips_mode,\ configure_crypto_policy
In the above example, four tags were selected as not remediated. A list of ansible-playbook tags may be listed like so.
ansible-playbook --list-tags rhel8-playbook-cui.yml 2>&1 |
grep "TASK TAGS" |
cut -d":" -f2 |
awk '{sub(/\[/, "")sub(/\]/, "")}1' |
sed -e 's/,//g' |
xargs -n 1 |
sort -u
For the ones specifically skipped in the example above.
[root@admin ansible]# ansible-playbook --list-tags rhel8-playbook-cui.yml 2>&1 | grep "TASK TAGS" | cut -d":" -f2 | awk '{sub(/\[/, "")sub(/\]/, "")}1' | sed -e 's/,//g' | xargs -n 1 | sort -u | egrep -i 'fips|accounts_passwords_pam'
accounts_passwords_pam_faillock_deny
accounts_passwords_pam_faillock_interval
accounts_passwords_pam_faillock_unlock_time
enable_fips_mode
Here are the truncated results. Using the time command, the script ran for 10 1/2 minutes.
PLAY RECAP ******************************************************************************************************** localhost : ok=316 changed=157 unreachable=0 failed=0 skipped=58 rescued=0 ignored=1
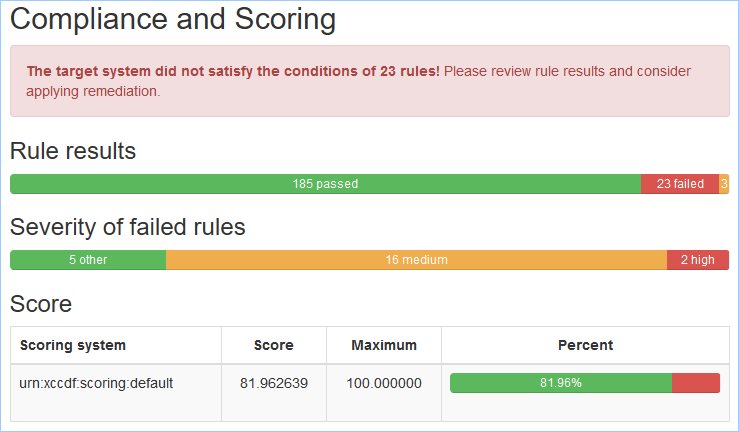
Running the same script to determine the number of remaining items to remediate; the number is reduced from 144 to 23.
[root@admin scap-security-guide-0.1.53]# oscap xccdf eval --profile xccdf_org.ssgproject.content_profile_cui ssg-rhel8-ds-1.2.xml 2>&1 | grep -i ^Result | grep fail | wc -l 23
Source(s)
- http://blog.leifmadsen.com/blog/2017/01/04/finding-available-ansible-tags-in-playbooks-and-roles/