A client suspected their computer of being infected with a virus, trojan, or malware. There was the inability of using Internet Explorer without being redirected. Antivirus and anti-malware applications either did not identify any infection or did an claimed to remove the infection. The systems persisted. In desperation the computer’s hard drive was brought to me to identify the problem and correct it.
A client suspected their computer of being infected with a virus, trojan, or malware. There was the inability of using Internet Explorer without being redirected. Antivirus and anti-malware applications either did not identify any infection or did an claimed to remove the infection. The systems persisted. In desperation the computer’s hard drive was brought to me to identify the problem and correct it.
Available was a USB sled, where I mounted the hard drive. Plugged the drive into another workstation. Before I do anything else, I proceed to clean the drive of temp files, dmp files, etc. The logic is that the files need to be removed anyway, so why waste the effort in scanning them for pests. This is a Microsoft Windows XP install.
Part 1 – Clean the drive
The folders I look into cleaning include:
Windows
- %WINDIR%\$NTServicePack*
- %WINDIR%\$NTUninstal*
- %WINDIR%\Minidump\*
- %WINDIR%\Prefetch\*
- %WINDIR%\SoftwareDistribution\*
- %WINDIR%\Temp\*
Documents and Settings
I repeat this process through each user profile that exists. Programs such as CCleaner only do the current user profile.
- %USERPROFILE%\%USERNAME%\Temp\*
- %USERPROFILE%\%USERNAME%\Temporary internet Files\*
- %USERPROFILE%\%USERNAME%\History\*
Since I have access to the drive via USB, the drive has not loaded it’s operating system, so access to System Volume Information (in this case) is accessible. I wanted to delete the contents of this folder, as it contains the System backups from System Restore. If there is a virus present, we do not want to restore it. Remember this is for Windows XP, do NOT do this on a Windows 2003 server as the System Volume Information is not the same.
System Volume Information (for Windows XP)
- C:\System volume Information\*.*
Finally, clean the contents of the RECYLER and RECYCLED bins on all drives.
This is far from a comprehensive list of all the files and folders that I manually delete, however, this will certainly narrow down the number of files to scan.
Part 2 – Manually and visually check files that may be out of place
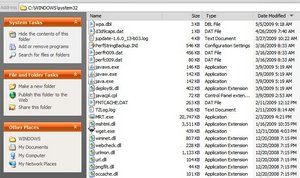
This part is less of a science and more of a skill developed through many years of cleaning computers of temp, virus, trojan, and malware files. I look at the system32 folder sort the folder by Date Modified and look at the most recent files. Generally most users do not install applications often, so I look at files that appear to be newer than the rest. I have also noted that the majority of the pests drop something in this folder.
The image provided above is from a clean system, however, is shown here to demonstrate the disparagy in file modification dates. Notice that the majority of the files are from December 2008 and back. So, if there is a problem, and the effects of this problem didn’t realize until recently, then a logical conclusion is that the offending file or files may exist in the remaining 20 or so files. From those files, I can quickly scan through them to determine if they are safe or not. Starting from the top and working downward, here is what I see:
- wpa.dbl – Microsoft activation file
- d3dcaps.dat – ???
- jupdate-1.6.0_13-b03.log – Java log
- PerfStringBackup.INI – Microsoft
- perfh009.dat – Microsoft
- perfc009.dat – Microsoft
- javaws.exe – Java
- javaw-exe – Java
- java.exe – Java
- deploytk.dll – I couldn’t readily identify this file, but the file date and time is the same as the other java*.exe files, so I can jump to the conclusion it is Java related.
- javacpl.cpl – Java
- FNTCACHE.DAT – Microsoft
- TZLog.log – Microsoft Terminal Services log
- MRT.exe – Microsoft pest cleaner
- mshtml.dll – Microsoft
Of course other files may exist, but this quick glance on this system indicates that the filesystem may be fine.
A deeper look into C:\Program files and so on may reveal differently. In the case of the clients computer, it did. There was a program that was installed one evening that was misspelled application (C:\Program Files\Quicky Plaeyr that contained one file Uninstall.exe. It didn’t look like a real application (however McAfee didn’t pick up on it) so I deleted it (after Googling Quicky Plaeyr to discover that this is the Zlob virus).
Remember this is not a complete guide by any means. It is a rough reference. If it looks complicated then you may consider someone else manually removing a virus or pest. However, if this rough foundation makes sense to you, I am certain you can find use for this information.