Configure Sendmail email server to use SSL encryption for sending/receiving email. This is an example of using a CA certificate rather than a self-signed certificate. This article assumes that the CA certificate is already in place and ready to go.
Modify the /etc/mail/sendmail.mc file. Find the section with similar variables that is commented out and copy this under it.
define(`confCACERT_PATH', `/etc/mail/certs/')dnl define(`confCACERT', `/etc/mail/certs/mycacert.ca-bundle')dnl define(`confSERVER_CERT', `/etc/mail/certs/mycacert.crt')dnl define(`confSERVER_KEY', `/etc/mail/certs/mycacert.key')dnl define(`confAUTH_OPTIONS',`A,p,y')dnl
At the bottom of the /etc/mail/sendmail.mc append the following lines or something similar to meet your needs. Applying ciphers are better than leaving them at default ciphers. The ones below is one of many possible examples. You will have better ratings by any online scanner.
LOCAL_CONFIG dnl# Do not allow SSLv2 and weak ciphers:dnl O CipherList=ALL:!aNULL:!ADH:!eNULL:!LOW:!EXP:RC4+RSA:+HIGH:+MEDIUM:-EDH-RSA-DES-CBC3-SHA:-EDH-DSS-DES-CBC3-SHA:-DES-CBC3-SHA:-DES-CBC3-MD5:+SSLv3:+TLSv1:-SSLv2
A note about ciphers. Determine if sendmail 8.11, 8.12, or 8.13 is compiled with _FFR_TLS_1. STARTTLS support was added in sendmail 8.11.
sendmail -d0.13 < /dev/null | grep FFR FFR Defines: _FFR_SMTP_SSL _FFR_TLS_1
Save the file and exit.
Make a directory and copy your certs into it. Then make sure that the certs are all 0600 perms.
mkdir -p /etc/mail/certs # copy your certs to /etc/mail/certs chmod 0600 /etc/mail/certs/*
The results of that directory using ls -Atlr /etc/mail/certs
-rw------- 1 root root 4104 May 5 23:43 mycacert.ca-bundle -rw------- 1 root root 1941 May 5 23:43 mycacert.crt -rw------- 1 root root 1763 May 5 23:43 mycacert.key
Restart sendmail.
service sendmail restart
Local Testing
On an earlier test, the 250-STARTTLS was not present. In that case, the reason, the certs had incorrect permissions. Upon setting them to 0600. All went well. I was able to track down this problem in the /var/log/maillog file.
May 6 00:04:46 web sendmail[6321]: STARTTLS=server: file /etc/mail/certs/mycacert.key unsafe: Group readable file
A successful implementation should result with a 250-STARTTLS.
[root@mywebsite~]# telnet localhost 25 Trying ::1... telnet: connect to address ::1: Connection refused Trying 127.0.0.1... Connected to localhost. Escape character is '^]'. 220 mycoolserver.com ESMTP Sendmail 8.14.4/8.14.4; Fri, 10 Jun 2016 12:45:16 -0400 ehlo localhost 250-mycoolserver.com Hello localhost.localdomain [127.0.0.1], pleased to meet you 250-ENHANCEDSTATUSCODES ... 250-STARTTLS ... 250 HELP quit
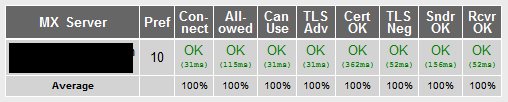
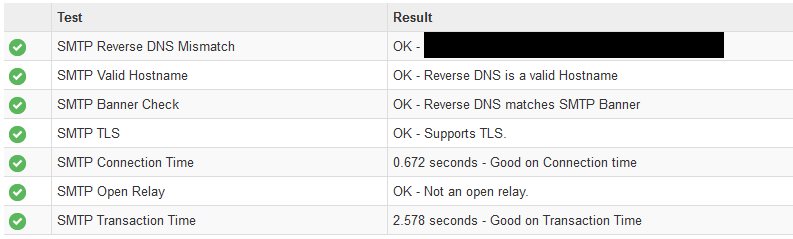
Test online.
http://www.checktls.com/perl/TestReceiver.pl
http://mxtoolbox.com/SuperTool.aspx
Source(s)
http://www.sendmail.org/~ca/email/starttls.html
http://www.cyberciti.biz/faq/howto-configure-sendmail-ssl-certificate-email/
http://aput.net/~jheiss/sendmail/tlsandrelay.shtml
http://cromwell-intl.com/linux/sendmail-ssl.html
http://www.sendmail.com/sm/open_source/docs/m4/starttls.html
http://www.thedumbterminal.co.uk/posts/2012/02/configuring_the_encryption_ciphers_used_with_sendmail.html
http://novosial.org/sendmail/cipherlist/index.html