DUO is a self-described “easy-to-use” two-factor authentication method that protects access to federated cloud and on-premises applications and servers. DUO offers several pricing plans and a free tier. The free tier is quite generous providing dual factor authentication to up to 10 users. This article assumes that you have created a DUO account, logged into the admin dashboard and ready to protect an application.
Protect an Application
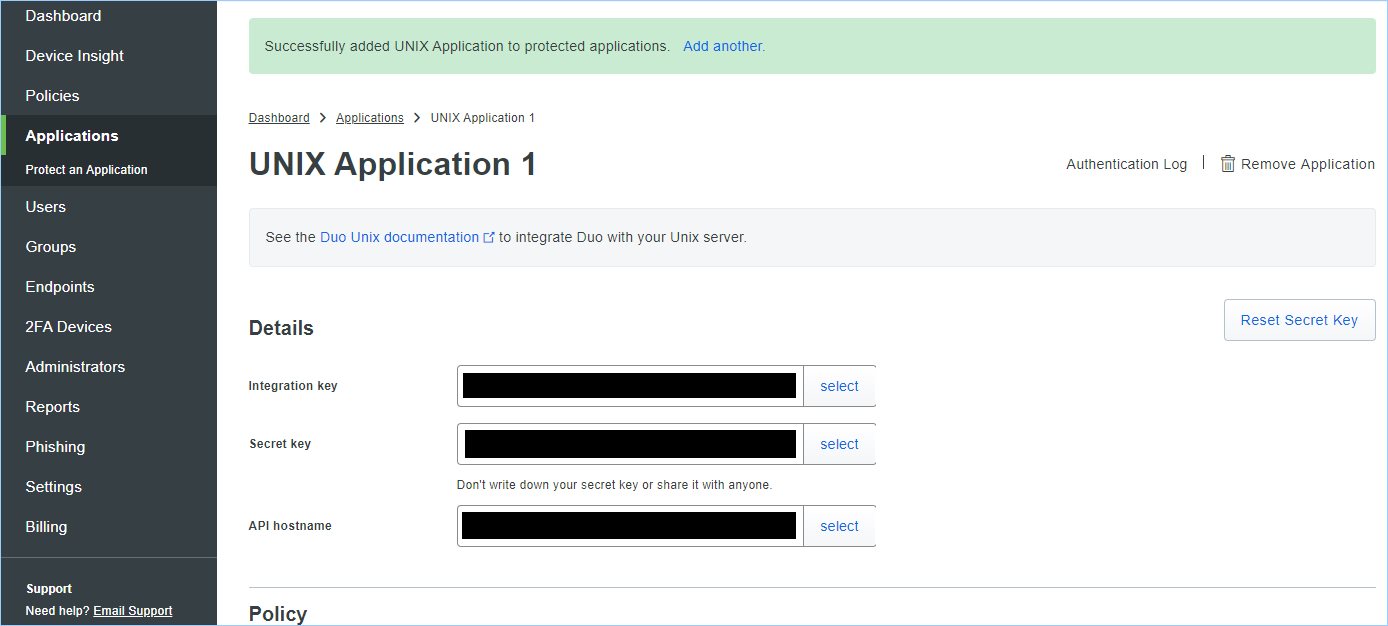
To protect an application or server, follow the steps below to create the Integration key, Secret key, and API hostname needed for the script and DUO.
- From the DUO Dashboard, select Applications, then Protect an Application
- Search for Unix Application
- Select Protect this Application
- Take note of the Integration key, Secret key, and API hostname.
The Script
Replace the integ_key, secret_key, and api_host values with the ones that was noted from above. Leave the quotes. You may notice that although there is an import of the GPG key, the yum install didn’t work (at least for me), and that is the reason the gpgcheck is set to zero. DUO updated the Duo GPG key for packages on supported distros on November 4, 2019. If you installed Duo before November 2019, use these commands to update the GPG key before the next time you install or upgrade Duo Unix.
#!/bin/bash integ_key="xxxxxxxxxxxxxxxxxxxxx" secret_key="xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx" api_host="api-xxxxxxxxxxxxxxxxxxxxx" cat << 'EOF'| tee /etc/yum.repos.d/duosec.repo
[duosecurity]
name=Duo Security Repository baseurl=http://pkg.duosecurity.com/CentOS/$releasever/$basearch enabled=1 gpgcheck=1 EOF rpm –import https://duo.com/DUO-GPG-PUBLIC-KEY.asc yum install duo_unix -y # Modify three configuration files sed -i.bak “s/ikey =/ikey = $integ_key/g” /etc/duo/pam_duo.conf sed -i “s/skey =/skey = $secret_key/g” /etc/duo/pam_duo.conf sed -i “s/host =/host = $api_host/g” /etc/duo/pam_duo.conf # echo ‘groups = addgroups, if you want’ >> /etc/duo/pam_duo.conf sed -i.bak ‘/#%PAM-1.0/a \auth required \/lib64\/security\/pam_duo.so’ /etc/pam.d/sshd sed -i.bak ‘/^ChallengeResponseAuthentication / s/no/yes/g’ /etc/ssh/sshd_config #Restart ssh systemctl restart sshd
A note about the groups setting above. If there is no groups specified then every user on this target server will require dual factor authentication, including root. If groups is added, then whatever groups that are listed and the users contained within them will require dual factor authentication. Further root should be locked down in the /etc/ssh/sshd_config to not permit root ssh access via PermitRootLogin no but you knew that.
Phone App
There is a phone app used for dual factor authentication. As stated above, this is assumed to be working.
Test
If the user account doesn’t already exist on the target server, create the user to match the name or alias associated with these api variables to logon. Then attempt to ssh into the target server. You should be prompted with a DUO authentication screen. Select DUO Push to phone and approve this action. This should follow with a password prompt. Done.
Source(s)
- https://duo.com/docs/loginduo